On Dormant Cyber Pathogens and Unicorns
On March 3, 2016 by Jonathan ZdziarskiGary Fagan, the Chief Deputy District Attorney for San Bernardino County, filed an amicus brief to the court in defense of the FBI compelling Apple to backdoor Farook’s iPhone. In this brief, DA Michael Ramos made the outrageous statement that Farook’s phone might contain a “lying dormant cyber pathogen”, a term that doesn’t actually exist in computer science, let alone in information security.
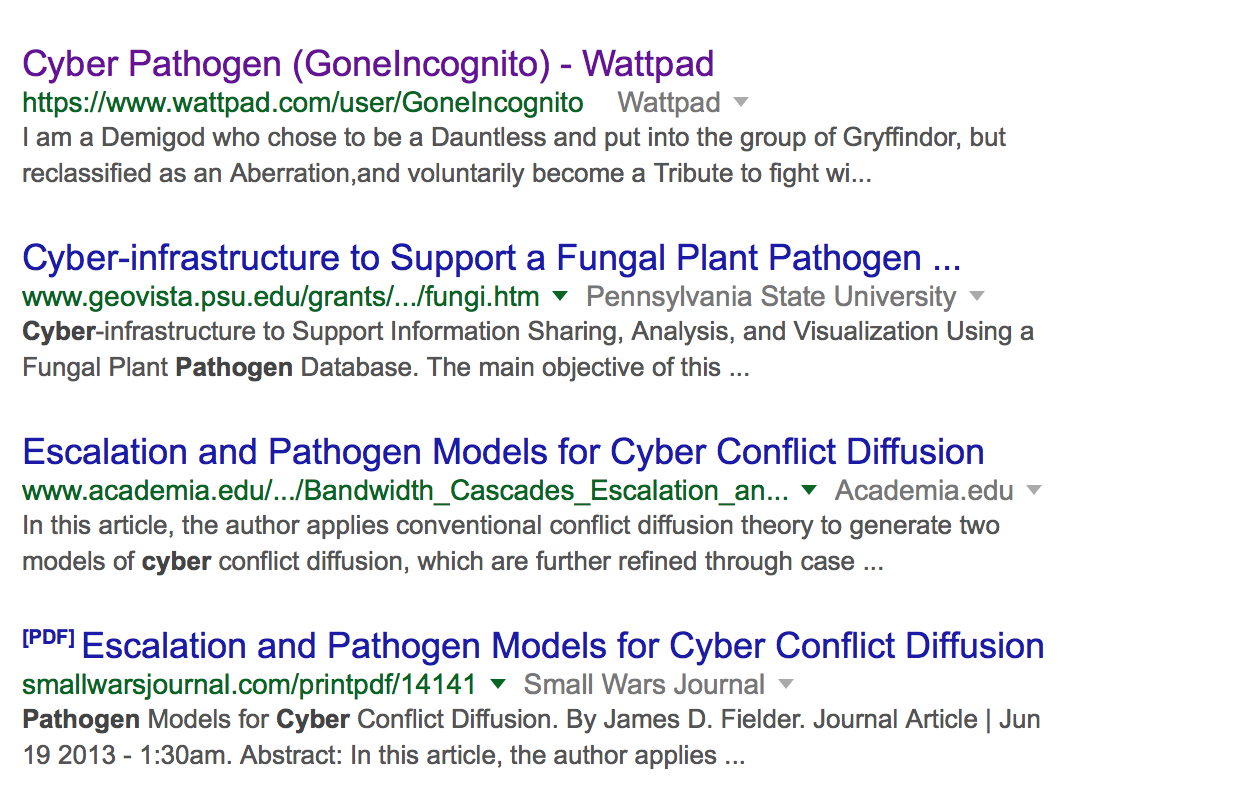
Let’s take a look at this term cyber pathogen. I was fortunate to have read this brief before it was publicly released in the news. I quickly googled the term “cyber pathogen” to see if anyone had used it in computer science. The first result was a hit on what appears to be Harry Potter fiction. That’s right, a Demigod from Gryffindor is the closest thing Google could find about cyber pathogens. The next several results show that Google is equally confused about the term, throwing out random results about fungus, academic pathogen models, and cyber conflicts. There is absolutely nothing in the universe that knows what a cyber pathogen is, except for Ramos apparently.
In information security, we have many widely accepted terms for network based threats. These include worms, viruses, backdoors; we have penetration tools, fuzzers, scanners, sniffers, etc. These are all very specific terms and they have a general consensus about their meaning. We don’t use dramatic and generalized terms like “pathogen”, and most people in information security even hate the term “cyber”. In fact, CSI: Cyber is not even bold enough to use wildly nonexistent terms like “cyber pathogen” in their scripts. Why? Because terms like this have no technical substance whatsoever, and will incite either fear or eye rolling (often the latter).
Ramos’s statements are not only misleading to the court, but amount to blatant fear mongering. They are designed to manipulate the court into making a ruling for the government, and in my opinion are egregious enough that Ramos should be held in contempt just for filing what amounts to a crazy apocalypse story.
Incidentally, Ramos’s statements are also self defeating to his cause, and damaging to the FBI’s case:
The Term “Dormant”
Dormant suggests that this “cyber pathogen” hasn’t actually become active on the network. The way Ramos worded it, he might also mean that it’s lying dormant on the phone. If it’s lying dormant on the phone, then what Ramos is really saying is that he has no proof whatsoever that they’ve been infected with anything. If he’s referring to the network, then by “dormant”, Ramos is saying that “maybe it hasn’t exploded on the network yet”. This is self-defeating, however, because in both cases, it makes the very clear statement that they have no evidence it exists.
On the one hand, if the county has identified the malicious code on their network, then there’s no need to get into the phone at all, because they’ve already got an unencrypted code sample that they can disassemble and reverse engineer, like malware researchers and teenagers all over the world do. On the other hand, if they haven’t identified it on the network, then that means there was never any infection at all, or that their security people are too incompetent to find it, leaving their network infected with an infection that hasn’t actually shown any evidence of itself.
So they either already have the code and don’t need the phone, or there is no code and this pathogen doesn’t exist. There’s no room here for a “ticking time bomb” if their security team is too incompetent to even find it on the network – because if they’re too incompetent to find it, they’re definitely going to be too incompetent to stop it.
While we’re at it, lets clear something up. Ethernet cables don’t have pathogens (or viruses, or worms). Systems do – computers, routers, switches, etc. If there really is any malicious code anywhere “on the network” then it should be traceable back to a system that can be forensically imaged and analyzed. There’s nowhere “in the wires” for a pathogen to get stuck and hide. It’s not like a real disease. It’s not even a real thing.
This Means Jailbreak
Next, lets take a look at how a cyber pathogen would work on an iPhone to begin with. Any serious kind of attack on a network would likely require raw packets or other forms of low level networking. The iPhone does not allow for PF_INET and SOCK_RAW, or other kinds of low level packets, to be used from within the app sandbox. It’s unlikely that Ramos knows this, however, and so his dramatic statements are actually damaging the FBI’s case, because the device would likely have to be jailbroken. Apple’s sandbox will simply not allow an application to abuse the network stack in such a way that would make a “cyber pathogen” feasible. The kind of dramatic network attack that the DA is trying to sell to Judge Pym would have to be big. Popular ports such as metasploit require a jailbroken device to work for this (and other) reasons, and any tool to inject something this serious would need the same.
A jailbroken iPhone means that the code signing on the device has already been compromised. There are a number of commercial forensics tools capable of imaging a jailbroken iPhone simply because this code signing barrier is out of the way… it also means that the one big piece to what the FBI is after (Apple’s code signing) isn’t in fact needed at all, and so Apple doesn’t even need to be involved in the FBI’s investigation. FBI can simply buy a forensics tool like Elcomsoft’s, or put their own ram disk together (like any teenager in the jailbreak community has done for years) to get access to the device. In fact, if the device is jailbroken, there’s a fair chance that they could even just ssh in using the default password, alpine, because hardly anyone ever changes it (NOTE: ssh can be forwarded over usbmuxd proxying, so it works when there’s no WiFi).
So if indeed the iPhone is being used to launch a never-before-seen low level cyber attack against Farook’s employer, then the iPhone itself is likely already jailbroken, and there’s simply no need to even involve Apple at all.
Encryption Isn’t a Problem
The iPhone’s operating system partition is not encrypted. Only the user data partition is encrypted. A jailbroken device that’s been retrofitted to attack a network is likely going to have a lot of low level code, some of which will reside on the operating system partition. Apple can image this partition and very easily see what code is running on it. I suspect they’ve already done this. If there were any evidence of malware targeting a network, not only would the FBI already know about it, but some of the code would likely not even be encrypted. And while the user data partition is encrypted, the file system itself is readable. Apple can dump the entire file structure of the device. Both Apple and the FBI already have the ability to know exactly what applications are installed on the device, what files exist, and while they can’t see the contents of user data files, they can certainly see if there’s any evidence of a metasploit installation or other such type of tool.
Magical Unicorns
So what of Ramos’s comments of a “lying dormant cyber pathogen” on the device? Well, he’s right about the lying part, but the rest sounds entirely made up.
Archives
- March 2024
- October 2023
- July 2023
- May 2023
- February 2023
- December 2022
- November 2022
- July 2022
- May 2022
- March 2022
- January 2022
- December 2021
- November 2021
- September 2021
- July 2021
- December 2020
- November 2020
- March 2020
- September 2019
- August 2019
- August 2018
- March 2018
- March 2017
- February 2017
- January 2017
- November 2016
- October 2016
- July 2016
- April 2016
- March 2016
- February 2016
- June 2015
- March 2015
- February 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- January 2014
- October 2013
- September 2013
- June 2013
- May 2013
- April 2013
- December 2012
- May 2012
- September 2011
- June 2011
- August 2010
- July 2010
- May 2010
- April 2010
- February 2010
- July 2009
- May 2008
- March 2008
- January 2008
- June 2007
- August 2006
- February 2006
Calendar
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 | ||