Counter-Forensics: Pair-Lock Your Device with Apple’s Configurator
On September 27, 2014 by Jonathan ZdziarskiLast updated for iOS 8 on September 28, 2014
As it turns out, the same mechanism that provided iOS 7 with a potential back door can also be used to help secure your iOS 7 or 8 devices should it ever fall into the wrong hands. This article is a brief how-to on using Apple’s Configurator utility to lock your device down so that no other devices can pair with it, even if you leave your device unlocked, or are compelled into unlocking it yourself with a passcode or a fingerprint. By pair-locking your device, you’re effectively disabling every logical forensics tool on the market by preventing it from talking to your iOS device, at least without first being able to undo this lock with pairing records from your desktop machine. This is a great technique for protecting your device from nosy coworkers, or cops in some states that have started grabbing your call history at traffic stops.
With iOS 8’s new encryption changes, Apple will no longer service law enforcement warrants, meaning these forensics techniques are one of just a few reliable ways to dump forensic data from your device (which often contains deleted records and much more than you see on the screen). Whatever the reason, pair locking will likely leave the person dumbfounded as to why their program doesn’t work, and you can easily just play dumb while trying not to snicker. This is an important step if you are a journalists, diplomat, security researcher, or other type of individual that may be targeted by a hostile foreign government. It also helps protect you legally, so that you don’t have to be put in contempt of court for refusing to turn over your PIN. The best thing about this technique is, unlike my previous technique using pairlock, this one doesn’t require jailbreaking your phone. You can do it right now with that shiny new device.
About Pairing Relationships
A pairing is a trusted relationship with another device, where a computer is granted privileged, trusted access on the iPhone. In order to have the level of control to backup the phone, download personal data, install applications, or perform other such tasks on an iOS device, the machine it’s connected to must be paired with the device. This is what iTunes and Xcode do to talk to the phone, but also what forensic imaging tools and a number of free hacking tools do as well. Once paired, these keys remain stored on the device indefinitely, until you perform a restore or wipe the phone some other way.
NOTE: As of iOS 8, you can reset all pairing relationships by using Settings > General > Reset > Reset Location & Privacy, or Reset Network Settings. This will delete your existing pairing relationship with your desktop (and all other computers), however it will not remove the pair-lock. This means you will have to remove the pair-lock in order to pair with your own desktop again. This can only be done using either Configurator’s supervisor certificates, or by entering a removal password that you may set when you set up the lock.
Pairing records can be used to access the phone even when it’s locked, over USB (and in iOS 7 and older, over WiFi). A pairing record is like a skeleton key to your iPhone or iPad. With it, someone can download all of your personal data from any application (including third party applications), install invisible applications (even onto your non-jailbroken phone) that run in the background, activate the device’s built-in packet sniffer to monitor your network traffic, and much more nefarious things. Much of this can also be done while the device is locked, regardless of whether you’re using a fingerprint reader or not, as long as you have a pairing record. Some level of personal data can also be acquired from the phone regardless of whether backup encryption is turned on or not, and a number of forensics tools and open source tools (like iMobileDevice) know how to get to this decrypted data.
Pair-Locking Explained
So what’s the best way to protect yourself from all of these? Pair-lock your device. By pair-locking your device, you’re preventing anyone from establishing a new trusted relationship with the device. So unless they’re able to steal the pair record your desktop has, they won’t be dumping data from your phone, installing malicious applications, or doing anything else to it – even if the phone leaves your physical possession, and even if you are compelled to give up the passcode, or unlock it with your fingerprint. When a device is unwilling to create a new pairing session with a desktop machine, nothing can talk to it through its proper interfaces – not forensics tools, not iMobileDevice tools, nothing. And that means unless you have a really old phone with a hardware exploit, there’s no way they’ll be able to dump data from it, since Apple’s no longer able to service warrants either for iOS 8 devices.
As I said, in order to get to the data on your device, you’ll need the pair record from your desktop. This means that you should be encrypting your desktop machine if you want to protect that relationship. It also means that you should be aware that you, yourself, will be unable to access your device if you lose this pairing record. On a Mac, you’ll find a copy of your pairing record in /var/db/lockdown. Guard it well… Maybe even off the computer if you don’t sync often.
One Big Caveat
I had previously documented a method to install profiles on the device without first supervising it, but it looks like the pair-lock feature does not carry over onto the device unless you have supervised it. Unfortunately, you’ll need to supervise your device in order to pair lock it.
One big caveat to supervising your device is that you cannot under any circumstances restore a backup of data from the device from before it was supervised, otherwise you’ll undo everything. What this means is that you have to start fresh, with a brand new install of iOS. There does not appear to be any way around this, meaning you’ll lose everything on the phone (and have to start from scratch).
If you decide later that you don’t want to supervise the device, you can, however restore an iTunes backup. This will blow away the supervised configuration, and also your pair lock, but it will let you restore all of your backed up content.
Getting Started
To get started, the first thing you’ll want to do is disconnect your iDevice from your computer, then Reset Location & Privacy. This will flush out any existing pairing relationships the phone has with other desktop machines. This is important, in the event that any existing pairings have been created that you don’t want (or might not know about).
Once you’ve reset privacy settings on the device, plug it back into your desktop computer, and it will establish a new pairing relationship with it again. This will create a file on your Mac in /var/db/lockdown with a filename named after the UDID of your device. If you don’t know what that is, you can open iTunes and click on the serial number of the phone to display the UDID. You might want to back up this pair record somewhere secure, as it will be the only one capable of talking to the phone.
One last thing you’ll want to do to get started it turn off Find my iPhone. Configurator won’t provision a device until you’ve done so; you can turn it back on once you’ve got everything set up.
Apple Configurator
Once you’ve got your pairing reset, download the latest Apple Configurator from the Mac App Store. This is a free download. This article has been updated specifically for Configurator 1.6 on iOS 8.
The Configurator is designed to enroll devices in enterprise (corporate) profiles, to place restrictions on them and allow them to be supervised by a security team. You’ll be using it to enroll your own device in your own private security policy.
Before you do anything to configure an iPhone, visit the Configurator’s Preferences, and turn off the feature that tells Configurator to uninstall applications that it doesn’t specifically install. If you don’t do this, then the next time you connect your device to Configurator, it will forcibly remove everything you’ve installed since you provisioned it (ouch!). Turn the following feature off before proceeding.
Create a Backup in Configurator
When a device is managed by with Configurator, you can’t restore from an iTunes backup. If you do, it will blow away the user data on the device, which includes your managed configuration (and pair lock). If you’d like to create an additional backup archive of your data before proceeding, you can do this in Configurator just to be safe.
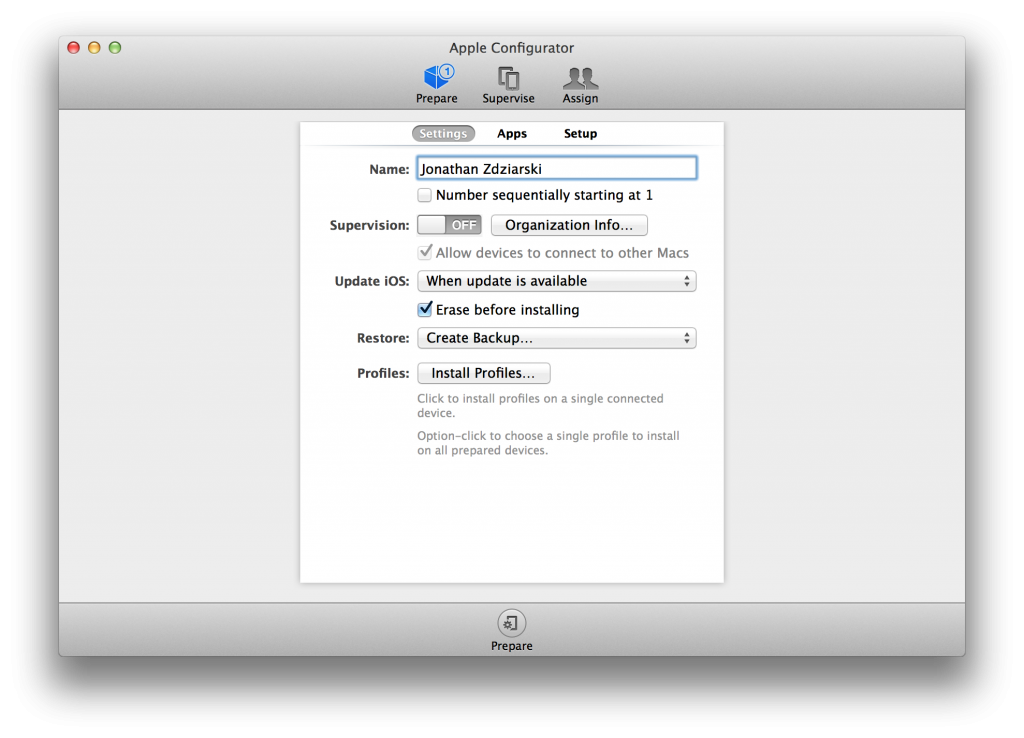
From the Restore menu, select the Create Backup option. This will prompt you to save a backup archive to your computer.

Prepare the Device
To manage a device, you’ll need to first prepare it. This will cause Configurator to erase the device completely, download and install the latest copy of iOS onto it, and “reset” the device into a supervised mode.
From the prepare screen, switch the Supervision switch to the on position. Your console should look similar to the one below.
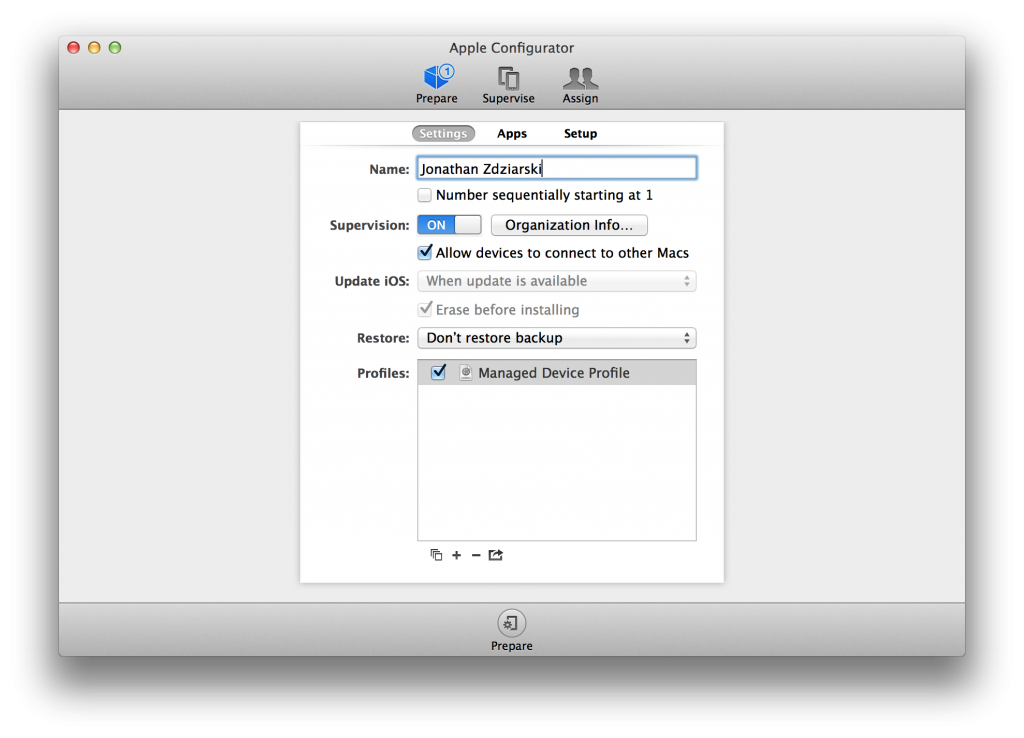
Decide if this machine is the only machine you’ll ever, and I mean ever, want to pair this phone with. If it is, then un-check the checkbox named, Allow devices to connect to other Macs. If, on the other hand, you might want to allow this phone to some day pair with other computers, then leave this box checked. I leave mine turned on, and instead manage that restriction through a profile, simply because my laptop could unexpectedly get stolen, or fail. In those cases, I can use the password removal option in the profile to remove the pair lock, so that I won’t have to erase my phone to un-manage it.
If you’ve opted to allow the device to (sometimes) connect to other computers, you’ll next want to create a profile, which you’ll use to lock and unlock the pairing. Enter a name for your supervision profile. I simply call mine “Managed Device Profile”.
Creating a Profile
Regardless of which option you use, you’ll create a new profile, which will contain your pairing restrictions. If you want to be able to remove the profile from the device, you can set a password required to remove it on the device, or for best security, select Never.
NOTE: If you live in, or plan to visit a country whose courts can compel you to give up your profile’s removal password, it would be best to select the Never option, so that you cannot be held in contempt of court for not giving up your password.
Next, click on the Restrictions tab and scroll down to the restriction titled Allow pairing with non-Configurator hosts (supervised only). This is your lock switch. To disable any new pairing with the device, uncheck this restriction. Later on, you’ll be able to edit this profile whenever you want to pair the device with a new host.
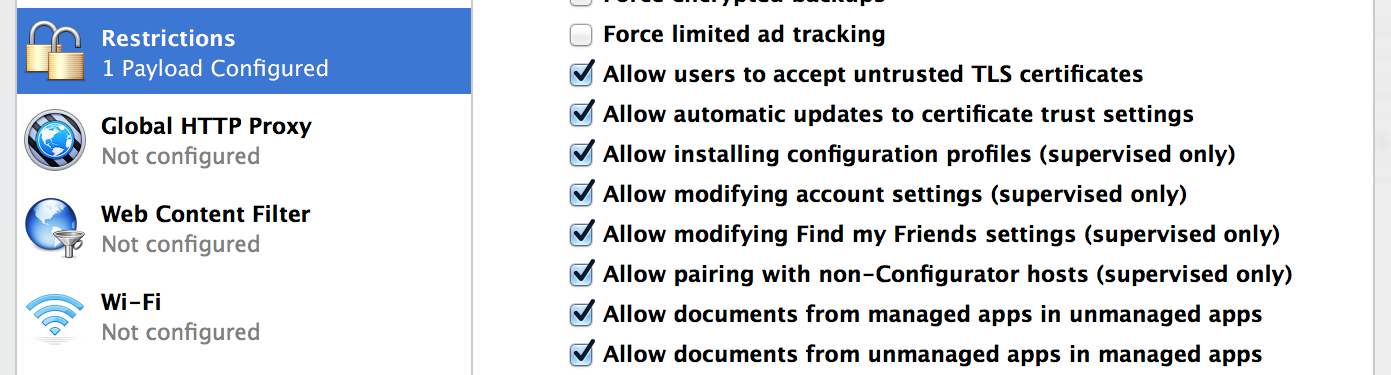
NOTE: Other restrictions, such as iCloud restrictions, can help to ensure that the device never backs up to the iCloud, or uses the photo stream option. It is also a good idea to force encrypted backups. You can enable these and other restrictions depending on the level of security you want to guarantee on the device.
Once you’ve finished making these changes, save the profile. If you’re simply installing it on a device as an unverified profile, the device will prompt you to install it.
When you are finished setting up the profile, click the Prepare button at the very bottom of the Configurator. The Configurator will then download and re-install the iOS firmware, then set up your device to be managed.
Post-Installation
Once the device comes back up, you’ll go through the usual setup process. Once setup is complete, your device should refuse to pair with any computer, even if it’s unlocked. You won’t be prompted to Trust anything, because it will simply fail. Even if you lose your device or are compelled into unlocking it, a logical dump should be impossible, because forensics tools won’t be able to pair with it. The system log on the device shows what’s happening internally:
Sep 19 23:53:59 lockdownd[52] <Notice>: 00241000 mc_allow_pairing: hostMayPairWithOptions said no Sep 19 23:53:59 lockdownd[52] <Notice>: 00241000 handle_pair: pair for BOGUS failed: PasswordProtected Sep 19 23:53:59 lockdownd[52] <Notice>: 00241000 set_response_error: handle_pair PasswordProtected
If you open up Settings on your device when view the Profiles under General, you should see your pairing profile, and a restriction preventing the device from pairing with any new devices.

If you set the profile up to be removable with a password (or Always, even), then you can remove the pairing lock at any time by just tapping remove. For ultimate security, set the removal to Never. Keep in mind, if you ever lose the supervisor certificates in your desktop’s keychain, you may have to wipe your device in order to get the pairing profile off of it, which also means that if you lose (or wipe) your laptop, you will not be able to talk to it with a new machine until you wipe.
Removing a Pairing Profile
Now lets say a few months go by and you decide you want to pair your device with a computer at work, or some other machine. If you set a removal password on the profile, you can enter that and simply remove the lock. If you didn’t, then you’ll only be able to remove the lock if you’ve supervised the device, which uses special supervisor certificates to authenticate on the device (stored on your keychain). To unlock the pairing in this fashion, you’ll need the computer you originally set this up with (unless you’ve backed up your pairing record and set up Configurator somewhere else). Launch the Configurator and click on the Supervise tab and click on your device.
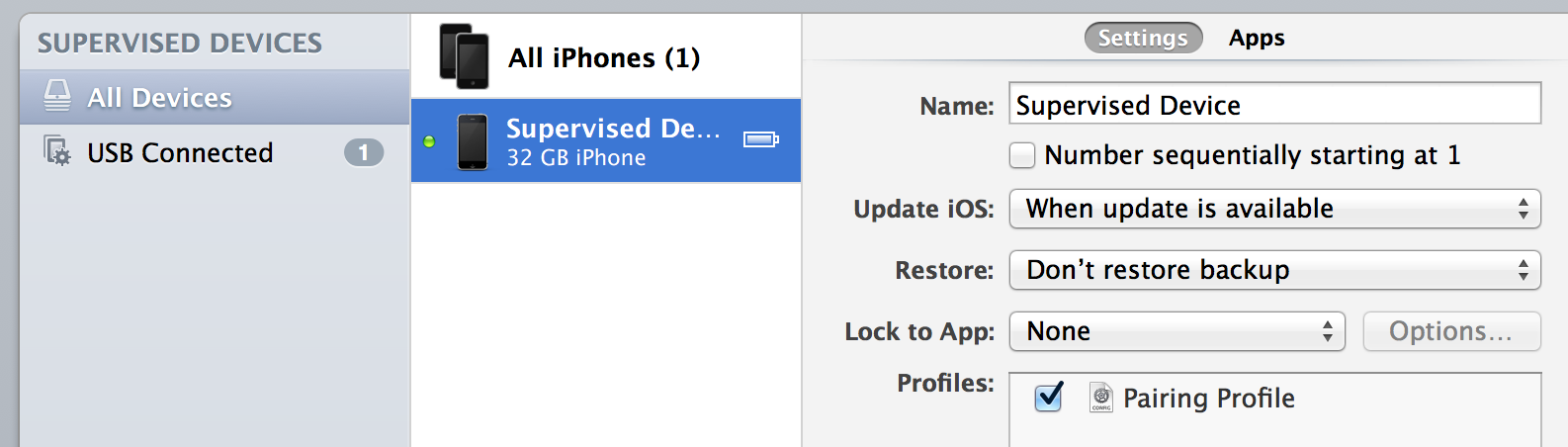
In the profiles window, you should see the Pairing Profile you created. Double-click on it, and bring up the same restrictions window you used to restrict pairing. Now, simply put a checkmark to allow pairing with non-Configurator hosts, and click Save. Click Refresh and revisit the setting to ensure that the change took. You can then disconnect your device and connect it up to any other machine to pair with it. (NOTE: If you run into issues, try power cycling the device for the setting to take). You should be prompted with a Trust dialog prior to pairing, just like old times. Just be sure to disable pairing again when you’re finished, using the same steps.
The advantage to this technique is very good pairing security. In fact, in order to remove the supervision profile, the intruder would need to erase the contents of your device. Someone would need to have physical possession to and full access to both your iOS device and your desktop computer in order to undo this pairing lock to perform a forensic extraction or any other kind of analysis.
The disadvantage is that you can’t simply decide you’re going to pair while you’re out somewhere. You can, if you made the profile removable, but then you’ll need to reinstall the profile to lock pairing again. Which will require a desktop. Pairing has to be a conscious decision, and takes time to verify that you have rights to the device’s content. Then again, shouldn’t it have always been this way? It’s a bit of a chore, but is well worth the added security.
Archives
- March 2024
- October 2023
- July 2023
- May 2023
- February 2023
- December 2022
- November 2022
- July 2022
- May 2022
- March 2022
- January 2022
- December 2021
- November 2021
- September 2021
- July 2021
- December 2020
- November 2020
- March 2020
- September 2019
- August 2019
- August 2018
- March 2018
- March 2017
- February 2017
- January 2017
- November 2016
- October 2016
- July 2016
- April 2016
- March 2016
- February 2016
- June 2015
- March 2015
- February 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- January 2014
- October 2013
- September 2013
- June 2013
- May 2013
- April 2013
- December 2012
- May 2012
- September 2011
- June 2011
- August 2010
- July 2010
- May 2010
- April 2010
- February 2010
- July 2009
- May 2008
- March 2008
- January 2008
- June 2007
- August 2006
- February 2006
Calendar
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 | ||