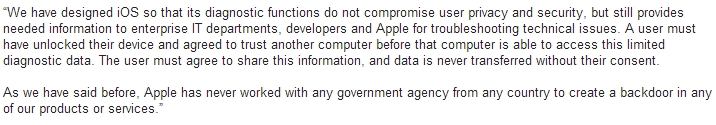
Apple Responds
On July 21, 2014 by Jonathan ZdziarskiIn a response from Apple PR to journalists about my HOPE/X talk, it looks like Apple might have inadvertently admitted that, in the most widely accepted sense of the word, they do indeed have backdoors in iOS, however claim that the purpose is for “diagnostics” and “enterprise”.
The problem with this is that these services dish out data (and bypass backup encryption) regardless of whether or not “Send Diagnostic Data to Apple” is turned on or off, and whether or not the device is managed by an enterprise policy of any kind. So if these services were intended for such purposes, you’d think they’d only work if the device was managed/supervised or if the user had enabled diagnostic mode. Unfortunately this isn’t the case and there is no way to disable these mechanisms. As a result, every single device has these features enabled and there’s no way to turn them off, nor are users prompted for consent to send this kind of personal data off the device.
A Major Supreme Court Ruling on its Way
On May 3, 2014 by Jonathan ZdziarskiI recently gave an interview with Forbes discussing the technical implications of a case recently heard by the Supreme Court about warrantless mobile phone searches. The technical reasons for not allowing this to go on are many, including the most severe penalty of potentially destroying evidence that you would otherwise need to prosecute a case (should the suspect be found to have committed a crime). There is a far more important dimension to this SCOTUS case, however; the ruling to come could potentially change the face of our constitutional rights as it pertains to data.
Recovering Photos From Bad Storage Cards
On March 17, 2014 by Jonathan ZdziarskiA Guide for Photogaphers, Not Geeks
Most photographers have had at least one heart attack moment when they realize all of the photos they’ve taken on a shoot (or a vacation) are suddenly gone, and there’s nothing on the camera’s storage card. Perhaps you’ve accidentally formatted the wrong card, or the card just somehow got damaged. If you’re a professional photographer, there’s a good chance your’e also not a forensic scientist or a hard-core nerd (although it’s OK to be all three!). That minor detail doesn’t mean, however, that you can’t learn to carve data off of a bad storage card and save yourself a lot of money on data recovery. While there are many aspects to forensic science that are extremely complicated, data carving isn’t one of them, and I’ll even walk you through how to do it on your Mac in this article, with a little bit of open source software and a few commands. If you’re scared of your computer, don’t worry. This is all very easy even though it looks a bit intimidating at first. You can test your skills using any old storage card you might have on hand. It doesn’t have to be damaged, although you might be surprised just how much data you thought was deleted from it!
First, lets talk about how your storage card works. When you plug your storage card into your computer, your computer looks for a list of files on the card; this is kind of like a rolodex of all the files your camera has stored. This “catalog” basically says, “OK, this file is this big, and it starts here”. You can think of it like the table of contents of a book. When you format a storage card, most of the time it’s just this table of contents that gets deleted; the actual bits and bytes from the photo you took aren’t erased (because that would take too long). The same can be true when the file system becomes damaged; in most cases, it’s just the file listing that gets blown up somehow, making it appear like there are no files on the card. In more extreme cases, physical damage can sometimes damage the data from one part of the card, but the data for the other half of the card can still be recovered; your computer needs to be told to look past all the damaged data, instead of just giving you an error message.
How to Tolerate DxO by Hacking MakerNotes and EXIF Tags
On January 22, 2014 by Jonathan ZdziarskiDxO Optics Pro was a purchase I immediately regretted making, once I realized that it intentionally restricts you from selecting what lens optics you’d like to adjust your photo with. It would take all of five minutes of programming to let the user decide, but for whatever stupid reason, if you’re using a different lens than the one they support OR if you are looking to adjust a photo that you’ve already adjusted in a different program, DxO becomes relatively useless.
I’ve figured out a couple easy ways to hack the tags in a raw image file to “fake” a different kind of lens. This worked for me. I make no guarantees it will work for you. In my case, I have a Canon 8-15mm Fisheye, which isn’t supported by DxO. The fixed 15mm Fisheye is, however, and since I only ever shoot at 15mm, I’d like to use the fixed module to correct. As it turns out, the module does a decent job once you fake DxO into thinking you actually used that lens.
On Expectation of Privacy
On April 25, 2013 by Jonathan ZdziarskiMany governments (including our own, here in the US) would have its citizens believe that privacy is a switch (that is, you either reasonably expect it, or you don’t). This has been demonstrated in many legal tests, and abused in many circumstances ranging from spying on electronic mail, to drones in our airspace monitoring the movements of private citizens. But privacy doesn’t work like a switch – at least it shouldn’t for a country that recognizes that privacy is an inherent right. In fact, privacy, like other components to security, works in layers. While the legal system might have us believe that privacy is switched off the moment we step outside, the intent of our Constitution’s Fourth Amendment (and our basic right, with or without it hard-coded into the Constitution) suggest otherwise; in fact, the Fourth Amendment was designed in part to protect the citizen in public. If our society can be convinced that privacy is a switch, however, then a government can make the case for flipping off that switch in any circumstance they want. Because no-one can ever practice perfect security, it’s easier for a government to simply draw a line at our front door. The right to privacy in public is one that is being very quickly stripped from our society by politicians and lawyers. Our current legal process for dealing with privacy misses one core component which adds dimension to privacy, and that is scope. Scope of privacy is present in many forms of logic that we naturally express as humans. Everything from computer programs to our natural technique for conveying third grade secrets (by cupping our hands over our mouth) demonstrates that we have a natural expectation of scope in privacy.
OnStar Reverses Privacy Decision: Or Did They?
On September 27, 2011 by Jonathan ZdziarskiOnStar today announced the reversal of their original decision to keep the customer’s data connection active to their vehicle after canceling service. The verbiage in the press release is ambiguous, however, and poses the question of whether OnStar is going to amend that specific portion of their new terms and conditions, or if they’re scrapping their new terms of conditions entirely.
If OnStar is only modifying this portion of their updated terms and conditions, then a major problem still exists: namely, the updated T&C, scheduled to go into effect in December 2011, would still grant OnStar broad new rights to collect the GPS positioning information about active customers, “for any purpose, at any time” and would still reserve OnStar the rights to sell access to this data to third parties.
A Few Words On Fear
On August 4, 2010 by Jonathan ZdziarskiFear is proof that what you fear hasn’t happened yet; if you still fear it, then the reality of it hasn’t manifested yet, therefore it isn’t real. Fear only exists because of love. You fear one thing because you love something else. Instead of putting so much energy into the fear side of it, why
Al Capone’s Original Thompson Machine Gun
On May 4, 2010 by Jonathan ZdziarskiJust when I thought my trip to Chicago would be average, some of the sergeants at the Chicago Police Training Academy, whom I’m training in iPhone forensic investigative methods, took me to the firing range in the basement and brought out an old dusty case. What came out of that case was an amazing piece
Handguns in Canada!
On April 22, 2010 by Jonathan ZdziarskiHow freaking awesome is this: After I finished a forensics workshop in liberal Canada, where civilians aren’t allowed to own or even possess handguns, the most awesome regional cops let me come in and shoot at their police range. We tore through about 200+ rounds wearing bullet proof vests (which are required while shooting) and
MIT Spam Conference 2008 Concludes
On March 28, 2008 by Jonathan ZdziarskiThe MIT Spam Conference concluded today with some great talks by various researchers in the field. I was particular sorry that I arrived late to miss Kathy Liszka’s talk on “Neural Networks for Image Spam”, as the tail end of it appeared very good. One thing I did notice that was quite refreshing about this